 Madison Ruppert
Madison Ruppert
Activist Post
According to documents recently obtained by the American Civil Liberties Union (ACLU), the Internal Revenue Service (IRS) believes they have the authority to read the private e-mail messages, Facebook chats and other online communications of Americans without obtaining a warrant.
This probably isn?t surprising given the blatant nature of the government?s illegal spying at this point and the complete flouting of judicial scrutiny when it comes to government surveillance.
According to IRS lawyers, the American people have ?generally no privacy? in online communications which means no Fourth Amendment standards apply and no search warrant is needed to read our private communications.
The 2009 IRS Search Warrant Handbook obtained by the ACLU through a Freedom of Information Act (FOIA) request claims that ?mails and other transmissions generally lose their reasonable expectation of privacy and thus their Fourth Amendment protection once they have been sent from an individual?s computer.?
Considering the fact that this so-called handbook was prepared by none other than the Office of Chief Counsel for the Criminal Tax Division, this is quite troubling.
While the ACLU?s intent was to obtain records simply stating if the IRS gets a warrant before reading email, text messages and other private electronic communications, the documents obtained don?t give a point blank answer.
While the IRS might not come right out and say it for obvious reasons, the ACLU notes that the 247 pages of records they obtained indeed suggest that the IRS reads private communications without getting a warrant first.
Saying ?suggest? is a quite conservative choice of words indeed given some of the material. Part of the 2009 handbook actually claims that ?the Fourth Amendment does not protect communications held in electronic storage, such as email messages stored on a server, because Internet users do not have a reasonable expectation of privacy in such communications.?
A 2010 presentation by the IRS Office of Chief Counsel claims that ?4th Amendment Does Not Protect Emails Stored on Server? and that there is ?No Privacy Expectation? when it comes to those emails.
However, United States v. Warshak, a 2010 case in the Sixth Circuit Court of Appeals, determined that the government must indeed obtain a probable cause warrant before forcing an email provider to release messages.
?However, the IRS hasn?t told the public whether it is following Warshak everywhere in the country, or only within the Sixth Circuit,? according to Nathan Freed Wessler, a staff attorney for the ACLU?s Speech, Privacy & Technology Project.
That said, it could not be clearer that the IRS policy before Warshak was to read electronic communications without ever obtaining a warrant.
The IRS apparently only follows the Electronic Communications Privacy Act (ECPA) a 1980s-era law that is far behind the times as CNET points out in writing that it was ?adopted in the era of telephone modems, BBSs, and UUCP links, long before gigabytes of e-mail stored in the cloud was ever envisioned.?
Full Article
CISPA Passes Markup Phase, But It Doesn?t Look Like Much Was Fixed
As expected, CISPA passed the House Intelligence Committee today after a closed markup session.
 by Leigh Beadon
by Leigh Beadon
Tech Dirt
April 11, 2013
The vote was 18-2, and according to Tony Romm at Politico, all of the amendments that were backed by the original authors of the bill were adopted.
If that?s the case, we?re talking about a bunch of changes that sound nice but don?t accomplish much, such as dropping the ?national security? provisions while broadening the definition of cybersecurity to encompass almost anything, requiring the government to remove personal information from shared data (once it?s already in the hands of the government), and explicitly preventing companies from using data they receive for marketing purpose.
(Which seems to go against previous insistence that the information shared would only be highly technical threat data).
CISPA is expected to go to the full house for a vote next week. As we get a closer look at the bill in its latest state, we?ll do a more detailed analysis ? but as it stands there?s little reason to believe that any of the core problems have been fixed (and we?re still waiting for someone to explain in clear, specific terms why this bill is needed at all).
Sen. Chuck Grassley: ?action may be needed to reconcile privacy and legitimate domestic drone use?
 Madison Ruppert
Madison Ruppert
Activist Post
Senator Chuck Grassley, an Iowa Republican, said that Congress may need to step in on behalf of the American people due to ?legitimate concern about insufficient safeguards in place to make sure drones aren?t used to spy on American citizens.?
This comes as the Florida Senate voted unanimous to restrict drone use, one small Minnesota city banned drones, Virginia considers a drone moratorium and a California city considers an anti-drone ordinance.
Similarly, Charlottesville, Virginia has already banned drones, the mayor of Seattle, Washington shot down their police department?s drone program and legislators across the country consider anti-drone laws.
Grassley, who is currently Iowa?s senior senator, has been quite critical of drone use in the United States in the past, saying that the government?s use of drones for domestic surveillance ?runs contrary to the nation of what it means to live in a free society.?
He apparently has not changed his position and has continued to question the disturbing rise of domestic drone use.
?The prospect of drone use inside the United States raises far-reaching issues concerning the extent of government surveillance authority and privacy in the digital age,? the report from Grassley?s office stated.
Indeed, the situation has devolved to the point that no one actually knows how many entities have been given the authority to fly drones domestically.
However, according to Adam B. Sullivan of the Press-Citizen, ?Grassley has made clear he doesn?t oppose the use of drones outright, saying he supports the technology for certain military and police operations.?
Yet still, Grassley said, ?There?s legitimate concern about insufficient safeguards in place to make sure drones aren?t used to spy on American citizens, perhaps unfairly enforce criminal law, and unduly infringe on individual privacy.?
?Congressional action may be needed to reconcile privacy and legitimate domestic drone use,? he added.
?As this technology develops, the sky is the limit on how drones could be used in our society, so it?s important that Congress be vigilant in addressing the balance of legitimate drone use and drone use that unduly interferes with private lives,? Grassley said.
Full Article
CISPA?s Sponsor Can?t Even Keep His Story Straight About NSA Having Access To Your Data
CISPA?s sponsors are doing the same thing they did last year when confronted with serious opposition to a terrible bill: they start lying about it.
 by Mike Masnick
by Mike Masnick
Tech Dirt
April 11, 2013
First, they released a ?fact vs. myth? sheet about the bill that was so ridiculously misleading that the EFF had to pick apart nearly every dubious claim. A big part of this is trying to hide the fact that the bill has very broad definitions that will make it much easier for the NSA to get access to private data. No one has claimed that this automatically allows the NSA to do full ?surveillance? via CISPA, but that?s what CISPA?s supporters pretend critics have said, so they can fight back against the strawman.
What?s incredible is that the statements from CISPA?s supporters are, themselves, quite contradictory. Take, for example, the hilarious statements from CISPA sponsor Mike Rogers to Politico, in which he seeks to ?fire back? at critics who worry about CISPA being used by the NSA. Read his comments carefully, and you?ll see that he goes from saying that the NSA won?t have anything to do with it, to saying that the definitions are broad (so that maybe the NSA will have something to do with it) to then saying that the NSA is the best at this, so it should be able to use CISPA to get access to private information. All within a matter of a few sentences.
Here?s the full bit from Rogers: ?I don?t know where they get that. It doesn?t say that in the bill. NSA is not authorized to monitor; this is not a surveillance bill. If you read the bill ? I encourage those privacy groups to actually read the bill ? you won?t find that in the bill. ? We?re agnostic on how the government would form [an info-sharing regime]; some want DHS, some want others. We thought, let?s be agnostic on that portion so you get the right regime. But if you don?t have the capability of the NSA, taking that information from the Iranians and the North Koreans and others, and allowing that to get back into the system, it?s worthless. And if you want the gold-standard protection from cyberattacks, the NSA has to be at least somewhere. They don?t have to get it, they don?t have to be the lead in it, but they?re the ones that have the capability for overseas collection.?
So, basically, it?s all an overstatement that the NSA might get access to your data? er? I mean, we don?t actually specify, so we?ll let the federal government make its own decisions later when its outside of public scrutiny and? oh yeah, of course we want the NSA to have access to the data, because they?re ?the gold-standard.?
?
?
EPIC files lawsuit against FBI to obtain documents about massive biometric identification database Madison Ruppert
Madison Ruppert
Activist Post
As I reported in 2011, the FBI is involved in collecting and storing the biometric identifiers of millions of Americans under their massive interagency Next Generation Identification (NGI) system. Now the Electronic Privacy Information Center (EPIC) has filed a lawsuit in an attempt to learn more.
Keep in mind, EPIC is responsible for exposing everything from Customs and Border Protection using drones in the U.S. capable of eavesdropping to details about the highly secretive ?Stingray? cell phone surveillance technology to DHS lying to Congress about their Big Brother policies to the NSA monitoring private U.S. computer networks to lies about body scanners to creepy DHS threat assessment technology to the fact that we?ll never know the true nature of the NSA-Google relationship and so much more.
According to a recent press release, EPIC, a Washington, D.C.-based non-profit, filed a Freedom of Information Act (FOIA) lawsuit after the FBI refused to respond to earlier FOIA requests seeking technical specifications and contracts for the system.
This is far from a minor issue, as EPIC pointedly notes in the complaint, ?When completed, the NGI system will be the largest biometric database in the world.?
The NGI is a multifaceted system that encompasses just about every biometric marker imaginable (though maybe not pedo-biometrics at this stage) and facial recognition technology is currently being rolled out in some unidentified areas.
Indeed, according to a July 18, 2012 FBI report, ?The NGI program?which is on scope, on schedule, on cost, and 60 percent deployed?is enabling the FBI to meet its criminal justice mission and continue to build its reputation as the global leader in biometrics.?
?NGI aggregates fingerprints, DNA profiles, iris scans, palm prints, voice identification profiles, photographs, and other identifying information,? according to EPIC, painting a troubling picture of what the system is capable of.
EPIC states that the FBI will use facial recognition technology ? which has become unbelievably fast ? to match images captured by surveillance cameras and other means with their massive database.
Of course, the fact that the FBI is sharing facial recognition technology with police departments across the United States helps the centralized database grow even faster.
We should not assume, however, that it will only be used for matching static images with the gigantic centralized database.
Indeed, if we can take a 2010 presentation by the FBI Biometric Center of Intelligence as any indicator, we can assume that it will be used for much more.
Full Article
CISPA Cyber Security Bill Moves Forward, IRS Says no Warrant Needed for Email Access
As the cyber security battle continues the IRS warns no warrant needed for email.
 by Derrick Broze
by Derrick Broze
Intellihub.com
April 11, 2013
The Cyber Intelligence Sharing and Protection Act (CISPA) passed through the? U.S. House Intelligence Committee by a vote of 18-2 on Wednesday evening.? The bill now goes to the full House for a vote as early as next week. The controversial measure was reintroduced in February after stalling in the Senate in 2012. Last year? President Obama issued a threat of presidential veto while activists protested nationwide.
The vote comes after a closed door meeting that was criticized by the Electronic Privacy Information Center (EPIC).? Jeramie Scott, national security fellow at EPIC? said ?Public accountability is paramount with cybersecurity. The House Intelligence Committee is trying to avoid public scrutiny. EPIC would like to see the process opened up to the public, robust privacy protections added, and Presidential Decision Directives on cybersecurity released to the public.?
EPiC are not alone in their opposition to the bill. The? the American Civil Liberties Union, the Electronic Frontier Foundation and companies such as Facebook and Reddit have spoken out about fears of giving government too much access to individuals private information. There is also the worry of supplying the National Security Agency with an even larger pool of names to spy on.
The Hill reported:
?The bill leaves it up to companies to decide which government entity they want to share cyber threat data with, although the NSA is among the list of agencies that the measure allows them to relay information to. CISPA would also enable companies to receive valuable government intelligence about cyber threats and grant them liability protection from legal action if they share threat data with the government.?
While opponents are concerned over privacy invasion supporters of the bill believe it is necessary? to protect American businesses from having trade secrets hacked away, as well as protecting critical infrastructure. House Intelligence Committee ranking member Dutch Ruppersberger (D-Md.) warned, ??We feel we have to move now. We don?t want another 9/11.?
Full Article
House committee approves pro-business cyber bill
By ANNE FLAHERTY, Associated Press | April 10, 2013 | Updated: April 10, 2013 6:43pm

WASHINGTON (AP) ? A House panel voted overwhelmingly Wednesday in favor of a new data-sharing program that would give the federal government a broader role in helping banks, manufacturers and other businesses protect themselves against cyberattacks.
The bill, approved 18-2 by the House Intelligence Committee, would enable companies to disclose technical threat data to the government and competitors in real-time, lifting antitrust restrictions and giving legal immunity to companies if hacked, so long as they act in good faith. In turn, companies could get access to government information on cyberthreats that is often classified.
It?s a defiant move by pro-business lawmakers who say concerns by privacy advocates and civil liberties groups are overblown. But even while the panel?s approval paves the way for an easy floor vote next week, the legislation has yet to be embraced outside the Republican-controlled House. Last year, a similar measure never gained traction and eventually prompted a White House veto threat.
?We?ve struck the right balance,? said Rep. Mike Rogers, R-Mich., the committee?s chairman. ?It?s 100 percent voluntary. There are no big mandates in this bill, and industry says under these conditions they think they can share (information), and the government can give them information that might protect them.?
The Cyber Intelligence Sharing and Protection Act, or CISPA, is widely backed by industry groups that say businesses are struggling to defend against aggressive and sophisticated attacks from hackers in China, Russia and Eastern Europe.
Privacy and civil liberties groups have long opposed the bill because they say it opens America?s commercial records to the federal government without putting a civilian agency in charge, such as the Homeland Security Department or Commerce Department. That leaves open the possibility that the National Security Agency or another military or intelligence office would become involved, they said. While the new program would be intended to transmit only technical threat data, opponents said they worried that personal information could be passed along, too.
Full Article
Supporters Say All The Wrong Things to Try and Pass CISPA
Ever since reintroducing CISPA, the so-called ?cybersecurity bill,? its supporters promote the bill with craftily worded or just plain misleading claims.
 By Mark M. Jaycox
By Mark M. Jaycox
EFF
April 9, 2013
Such claims have been lobbed over and over again in op-eds, at hearings, and in press materials. ?One ?fact sheet? by Rep. Rogers and Ruppersberger titled ?Myth v. Fact? is so dubious that we felt we had to comment. To stop this type of misinformation?and to stop CISPA?we urge you to tell your members of Congress to stand up for privacy.
Here are some of the statements supporters of CISPA are pushing and why they?re false:
Supporters of CISPA say, ?There are no broad definitions?
Supporters are keen to note that the bill doesn?t have broad definitions. In the ?Myth v. Fact? sheet, the authors of CISPA specifically point to the definition of ?cyber threat information.? Cyber threat information is information about an online threat that companies can share with each other and with any government agency?including the NSA. In hearings, experts have said that they don?t need to share personally identifiable information to combat threats. But the definition in the bill allows for any information related to a perceived threat or vulnerability?including sensitive personal information?to be shared. Cyber threat information should be a narrowly defined term.
Another example of a broad (or missing) definition is the term ?cybersecurity system.? ?Companies can use a ?cybersecurity system? to ?identify or obtain? information about a potential threat (?cyber threat information?). The definition is critical to understanding the bill, but is circular. ?CISPA defines a ?cybersecurity system? as ?a system designed or employed? for a cybersecurity purpose (i.e. to protect against vulnerabilities or threats). The language is not limited to network security software or intrusion detection systems, and is so broadly written that one wonders if a ?system? involving a tangible item?e.g., locks on doors?could be considered a ?cybersecurity system.?? In practical terms, it?s unclear what is exactly covered by such a ?system,? because the word ?system? is never defined.
The best example of a dangerous undefined term in the bill is found within the overly broad legal immunity for companies. The clause grants a company who acts in ?good faith? immunity for ?any decisions made? based off of the information it learns from the government or other companies. Does this cover decisions to violate other laws, like computer crime laws? Or privacy laws intended to protect users? Companies should not be given carte blanche immunity to violate long-standing computer crime and privacy law. And it is notoriously hard to prove that a company acted in bad faith, in the few circumstances where you would actually find out your privacy had been violated.
Full Article
Is Facebook?s Smartphone Just a New Way to Collect Data About You?
Mark Guarino
Christian Science Monitor
April 5, 2013
Using Facebook on your phone? Soon, the company will make it much easier, but, some say, at a steep cost to your privacy.
That?s the tradeoff as the social media giant announces on Thursday that it is launching a branded smartphone that will reportedly operate on software called Facebook Home. Unlike the current Facebook app that allows users to access the site, the new Facebook phone will further integrate the software into features such as text messaging, photo uploading, and more.
As more consumers transition their online habits from desktop computers to smartphones and tablets, advertisers are following. The phone allows Facebook to tap into the lucrative US mobile advertising market that is expected to be worth $7.29 billion by the end of 2013, according to eMarketer.
Read full article
DEA Accused Of Leaking Misleading Info Falsely Implying That It Can?t Read Apple iMessages
This is an update on yesterday?s story about the DEA and encrypted Iphone messaging.
 by Mike Masnick
by Mike Masnick
Tech Dirt
April 5, 2013
So this is interesting. Yesterday, CNET had a story revealing a ?leaked? Drug Enforcement Agency (DEA) memo suggesting that messages sent via Apple?s own iMessage system were untappable and were ?frustrating? law enforcement. Here?s a snippet from that article:
Encryption used in Apple?s iMessage chat service has stymied attempts by federal drug enforcement agents to eavesdrop on suspects? conversations, an internal government document reveals.
An internal Drug Enforcement Administration document seen by CNET discusses a February 2013 criminal investigation and warns that because of the use of encryption, ?it is impossible to intercept iMessages between two Apple devices? even with a court order approved by a federal judge.
CNET posted an image of the letter:

That leads Sanchez to wonder if there might be some sort of ulterior motive behind the ?leaking? of this document, done in a way to falsely imply that iMessages are actually impervious to government snooping. He comes up with two plausible theories: (1) that this is part of the feds? longstanding effort to convince lawmakers to make it mandatory that all communications systems have backdoors for wiretapping and (2) that it?s an attempt to convince criminals that iMessages are safe, so they start using them falsely believing their messages are protected.
Which brings us to the question of why, exactly, this sensitive law enforcement document leaked to a news outlet in the first place. It would be very strange, after all, for a cop to deliberately pass along information that could help drug dealers shield their communications from police. One reason might be to create support for the Justice Department?s longstanding campaign for legislation to require Internet providers to create backdoors ensuring police can read encrypted communications?even though in this case, the backdoor would appear to already exist.
The CNET article itself discusses this so-called ?Going Dark? initiative. But another possible motive is to spread the very false impression that the article creates: That iMessages are somehow more difficult, if not impossible, for law enforcement to intercept. Criminals might then switch to using the iMessage service, which is no more immune to interception in reality, and actually provides police with far more useful data than traditional text messages can. If that?s what happened here, you have to admire the leaker?s ingenuity?but I?m inclined to think people are entitled to accurate information about the real level of security their communication enjoy.
While both scenarios are plausible, both seem fairly cynical as well. I?d like to think that law enforcement is above attempting such tricks, but unfortunately that might just be naive these days.
AG Holder grants secret powers to collect files on innocent Americans
Monday, April 01, 2013 by: J. D. Heyes
 (NaturalNews) During his tenure as head of the FBI, J. Edgar Hoover used the power of his office and his agency to intimidate and harass political dissenters, silence activists and to collect secret files on scores of political opponents and U.S. citizens in general. Hoover died in 1972 but it looks like he has been succeeded by U.S. Attorney General Eric Holder, head of the Justice Department, which includes the FBI.
(NaturalNews) During his tenure as head of the FBI, J. Edgar Hoover used the power of his office and his agency to intimidate and harass political dissenters, silence activists and to collect secret files on scores of political opponents and U.S. citizens in general. Hoover died in 1972 but it looks like he has been succeeded by U.S. Attorney General Eric Holder, head of the Justice Department, which includes the FBI.
In a secret decree granted without debate or approval from Congress, Holder recently granted the National Counterterrorism Center a wide range of new powers to keep dossiers and secret files on U.S. citizens, even if they aren?t suspected of committing a crime, The Wall Street Journal reports.
The paper said that earlier this year, Holder granted the center the ability to copy entire government databases that held information on such intimate details like flight records, lists of casino employees, Americans hosting foreign-exchange students and other personal data for up to five years, even if there was never any suspicion that persons in those databases committed any crimes.
Full Article
U.S. government plans to scan your private emails using cybersecurity program as a cover
Monday, April 01, 2013 by: J. D. Heyes
(NaturalNews) As mainstream political and media figures head-fake the country with near wall-to-wall coverage of whether men and women should be allowed to marry each other, the U.S. government is planning to snoop through more and more of your private email, using the ?threat of cyber terrorism? as its excuse.
Reports in recent days say the additional snooping will come in the form of an expanded cyber security program designed to scan Internet traffic heading into and out of defense contractors; the scanning will ?include far more of the country?s private, civilian-run infrastructure,? NBC News reported.
That means that more private sector employees than at any previous time ? including employees of utilities, big banks, key transportation companies and others ? will have emails and web browsing scanned, as a cyber security precaution.
Congress isn?t to blame for this latest assault on privacy. This one comes in the form of an executive order on cyber security issued by President Obama in February. Under the order, scans will be driven by classified information provided by the U.S. intelligence community ? including data from the National Security Agency - on new or serious espionage threats and hacking attempts. In mid-March, the heads of U.S. spy agencies said cyber attacks have replaced terrorism as the nation?s top threat.
Full Article
(U//FOUO) DHS Cybersecurity Executive Order 13636 Critical Infrastructure Presentation
Public Intelligence
March 31, 2013 in Department of Homeland Security

Executive Order 13636: Improving Critical Infrastructure Cybersecurity Cyber-Dependent Infrastructure Identification Working Group (CDIIWG)
- 20 pages
- For Official Use Only
- March 11, 2013
![]()
Overview of Executive Order 13636
- Executive Order (EO) 13636, Improving Critical Infrastructure Cybersecurity was released on February 12, 2013
- Relies on public-private collaboration to improve critical infrastructure cyber posture
- Includes elements to enhance information sharing, develop a cybersecurity framework, and create a voluntary cybersecurity program
- Requires the Department of Homeland Security (DHS) to identify the ?critical infrastructure where a cybersecurity incident could reasonably result in catastrophic regional or national effects on public health or safety, economic security, or national security?
DHS will work with CIPAC to execute Section 9 of the EO
?Within 150 days of the date of this order, the Secretary shall use a risk-based approach to identify critical infrastructure where a cybersecurity incident could reasonably result in catastrophic regional or national effects on public health or safety, economic security, or national security.? (EO 13636, Section 9)
Apply consistent, objective criteria
Stakeholders include:
? Critical Infrastructure Partnership Advisory Council (CIPAC)
? Sector Specific Agencies (SSA)
? Sector Coordinating Councils (SCC)
? Government Coordinating Councils (GCC)
? Critical infrastructure owners and operators
The list of identified critical infrastructure will be reviewed and updated on an annual basis
Execution of Section 9 will be led by the Cyber-Dependent Infrastructure Identification Working Group (CDIIWG)
Overview of CDII Approach (1 of 2)
Only a small subset of U.S. infrastructure will fall under the focus of the EO activity
? Owners and operators will have the opportunity to provide relevant information
? A review process will be established for the identification as critical infrastructure
Focus is on critical infrastructure that could be compromised through cyber exploitation and which, if incapacitated, could result in catastrophic national, public health, or economic consequences
? Higher standard than debilitating, which is what is used in the base definition to define critical infrastructure
? The Secretary of DHS will provide a list of critical infrastructure most at risk in the context of a cyber incident within 150 days of EO release
? Commercial IT products and consumer information technology services will not be directly designated under the EO as infrastructure most at risk
All sectors will be engaged ?through engagement and initial analysis it may be determined that a sector does not have any infrastructure that meets the threshold, the focus of the initial list will not be on that sector(s)
Full Article
Fusion Center Director: We Don?t Spy on Americans, Just Anti-Government Americans
Law enforcement intelligence-processing fusion centers have long come under attack for spying on Americans. The Arkansas director wanted to clarify the truth: centers only spies on some Americans ? those who appear to be a threat to the government.

(Photo by Oli Scarff/Getty Images)
RT
March 31, 2013
In trying to clear up the ?misconceptions? about the conduct of fusion centers, Arkansas State Fusion Center Director Richard Davis simply confirmed Americans? fears: the center does in fact spy on Americans ? but only on those who are suspected to be ?anti-government?.
?The misconceptions are that we are conducting spying operations on US citizens, which is of course not a fact. That is absolutely not what we do,? he told the NWA Homepage, which supports KNWA-TV and Fox 24.
After claiming that his office ?absolutely? does not spy on Americans, he proceeded to explain that this does not apply to those who could be interpreted as a ?threat? to national security. Davis said his office places its focus on international plots, ?domestic terrorism and certain groups that are anti-government. We want to kind of take a look at that and receive that information.?
But the First Amendment allows for the freedom of speech and opinion, making it lawfully acceptable for Americans to express their grievances against the US government. The number of anti-government groups even hit a record high in 2012, according to the Southern Poverty Law Center. Many of these groups are ?hate groups? that express disdain for minorities. But unless they become violent, these groups are legally allowed to exist.
?We are seeing the fourth straight year of really explosive growth on the part of anti-government patriot groups and militias,? Mark Potok, senior fellow at the SPLC, told Mother Jones. ?That?s 913 percent in growth. We?ve never seen that kind of growth in any group we cover.?
And with a record-high number of anti-government groups, fusion centers may be spying on more Americans than ever before ? or at least, have the self-proclaimed right to do so.
?I do what I do because of what happened on 9/11,? Davis said. ?There?s this urge and this feeling inside that you want to do something, and this is a perfect opportunity for me.?
But Davis? argument is flawed: in order to determine whether or not someone is considered a threat to national security, fusion centers would first have to spy on Americans to weed out the suspected individuals, and then proceed to spy on the ?anti-government? individuals further.
Full Article
Seattle Police surveillance cameras: even after FOIA request fulfilled, important questions remain
 Madison Ruppert
Madison Ruppert
Activist Post
Even after a Freedom of Information Act (FOIA) request was fulfilled by the Seattle Police Department, massive questions remain unanswered about their plans to activate an expansive surveillance camera network ? though it appears to be far short of systems like SkyCop.
Thankfully, the SPD?s attempt to put the cameras in place was met with a great deal of criticism from the community, much like their planned drone program. If the successful effort to shut down the department?s drone program is any indicator, we can be optimistic about this newest surveillance system.
The surveillance system ? much like those in New York City, San Francisco and elsewhere, including ones placed directly in front of residences ? was installed without public input, according to an article by The Seattle Times.
While the SPD originally planned on having the system activated by March 31, 2013, the public outcry led to an indefinite delay.
The system was originally described as ?port security? during a May 2012 city council meeting discussing the $5 million grant funding the program, but this is clearly not restricted to port security, as shown by a map obtained via FOIA request.
Furthermore, West Seattle Blog points out that ?police also have talked about other ways they, Seattle Fire, and others plan to use the camera system in developing public-safety situations? beyond the port security application.
At a March 12 public meeting, SPD also indicated that they may post images captured from the cameras publicly online with frames refreshing around every two minutes.
Seattle Mayor Michael McGinn told West Seattle Blog that the surveillance system ?will not be operated without a thorough public vetting,? but what that vetting will actually entail remains a mystery.
Thus far ?it has consisted of a briefing before the Seattle City Council?s Public Safety, Civil Rights, and Technology Committee on February 20th (WSB coverage here), a briefing at the Alki Community Council?s February 21st board meeting (WSB coverage here), an SPD-led briefing/Q-A session at Alki Bathhouse on March 12th (WSB coverage here, with video of the entire meeting), and a similar session one week later at Belltown Community Center.?
Full Article
Zero Privacy? FBI to spy in real-time on web chats
Youtube
Web users? online communications may be about to get a wider and possibly unwanted audience. The FBI is seeking more powers to spy on people?s emails and internet chats in real time. The proposals have already been met with criticism, that they are a complete breach of privacy.
This Is Not The Cloud Computing We Should Have
Even though I was never a big Google Reader user, its death has got me thinking about online services quite a bit lately ? and really reminded me that we?ve done the cloud wrong. Rather than build true cloud computing, we?ve built a bunch of lockboxes.

by Mike Masnick
Tech Dirt
March 30, 2013
The cloud was supposed to free us, not lock us in
?Cloud computing? went by a variety of other terms in the past before this marketing term stuck, but the key part of it was that it was supposed to free us of worrying about the location of our data. Rather than having to have things stored locally, the data could be anywhere, and we could access it via any machine or device. That sort of happened, and there definitely are benefits to data being stored in the cloud, rather than locally. But? what came with today?s ?cloud? was a totally different kind of lock: a lock to the service.
Full Article
CIA Chief Technology Officer Big Data and Cloud Computing Presentations
Public Intelligence
March 29, 2013 in Central Intelligence Agency
The following are presentation slides for talks given by Ira A. ?Gus? Hunt, the CIA?s Chief Technology Officer, on the topic of ?big data? and cloud computing.? A presentation given by Hunt at the GigaOM Structure:Data conference last week garnered significant attention for his discussion of the CIA?s desire to ?collect everything and hang on to it forever.?? Hunt?s presentation was similar to several he has given before, many of which share the same slides, including one which states: ?It is really very nearly within our grasp to be able to compute on all human generated information.?
| Beyond Big Data: Riding the Technology Wave | March 2012 | 33 pages | Download |
| Big Data Challenges and Opportunities | March 2012 | 23 pages | Download |
| Big Data Operational Excellence Ahead in the Cloud | October 2011 | 24 pages | Download |


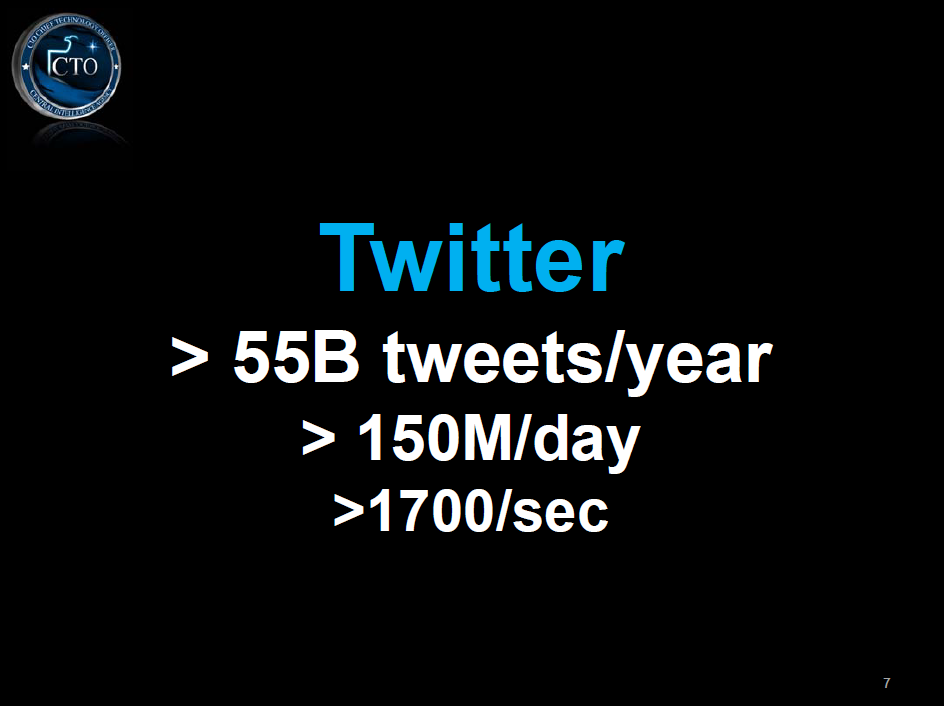
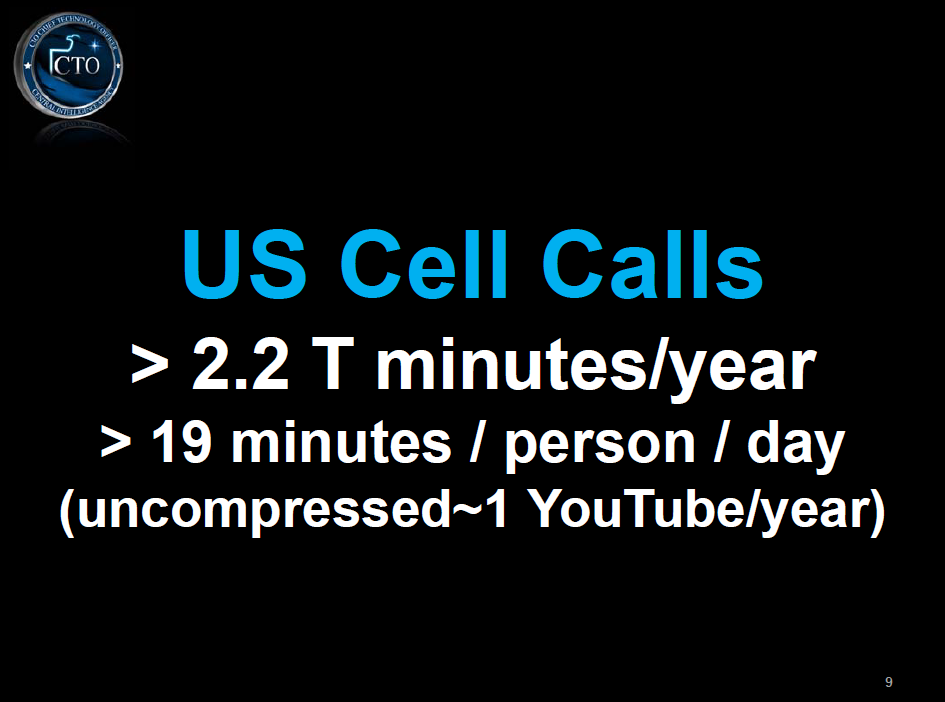
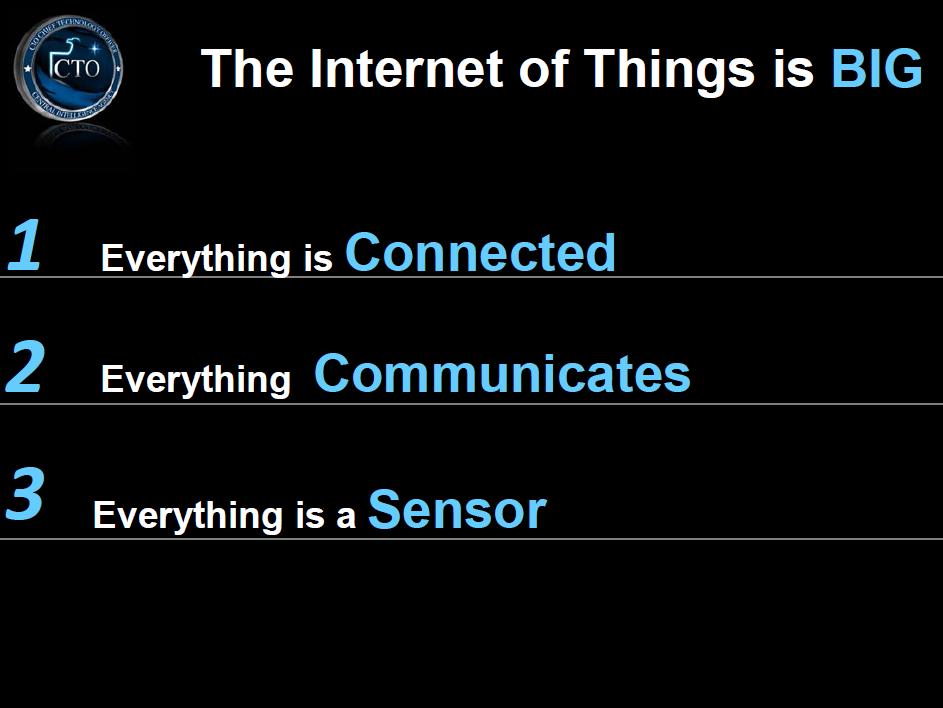


Full Article
When a Secretive Stingray Cell Phone Tracking ?Warrant? Isn?t a Warrant
(ACTIVIST POST)?? An Arizona federal court this afternoon will be the battleground over the government?s use of a ?Stingray??surveillance device in a closely watched criminal case, United States v. Rigmaiden. And in an important development, new documents revealed after an ACLU of Northern California Freedom of Information Act (FOIA) request should leave the government with some explaining to do.
?Stingray? is the brand name of an International Mobile Subscriber Identity locator, or ?IMSI catcher.? A Stingray acts as a fake cell-phone tower, small enough to fit in a van, allowing the government to route all network traffic to the fake tower. We?ve warned that Stingrays are dangerous because they have the capability to obtain the contents of electronic and wire communications while necessarily sucking down data on scores of innocent people along the way.
The Fourth Amendment requires searches be ?reasonable,? generally meaning they must be accompanied by a warrant. To get a warrant, the government must show there is probable cause to believe the place they want to search will have evidence of a crime. And it means the judge must issue ensure the warrant is ?particular,? or limited to only allow searches into areas where the evidence is most likely to be found. The only way a judge can make these tough decisions is with the government being forthright about what it?s doing.
But when it comes to Stingrays the government has been extremely secretive about its use, withholding documents in FOIA requests, failing to explain or even understand the technology to a Texas federal judge, and in Rigmaiden, misleading the court about the fact it?s even using one at all.
Daniel David Rigmaiden is charged with a variety of tax and wire fraud crimes. Hoping to pinpoint Rigmaiden?s precise location within an apartment complex, federal agents applied for an order requesting the court to order Verizon to help the agents pinpoint the physical location of a wireless broadband access card and cell phone they believed Rigmaiden was using. The order is clearly directed towards Verizon:
The Court therefore ORDERS, pursuant to Federal Rule of Criminal Procedure 41(b); Title 18, United States Code, Sections 2703 and 3117; and Title 28, United States Code, Section 1651, that Verizon Wireless, within ten (10) days of the signing of this Order and for a period not to exceed 30 days, unless extended by the Court, shall provide to agents of the FBI data and information obtained from the monitoring of transmissions related to the location of the Target Broadband Access Card/Cellular Telephone?
Ultimately, it turns out the government did not just get Verizon to give it the data. It also used a Stingray device to find Rigmaiden, sucking up loads of other data from other electronic devices in the complex as well, which it deleted.
When Rigmaiden filed a motion to suppress the Stingray evidence as a warrantless search in violation of the Fourth Amendment, the government responded that this order was a search warrant that authorized the government to use the Stingray.
Together with the ACLU of Northern California and the ACLU, we filed an amicus brief in support of Rigmaiden, noting that this ?order? wasn?t a search warrant because it was directed towards Verizon, made no mention of an IMSI catcher or Stingray and didn?t authorize the government?rather than Verizon?to do anything.
Plus to the extent it captured loads of information from other people not suspected of criminal activity it was a ?general warrant,? the precise evil the Fourth Amendment was designed to prevent.
The FOIA documents bolster our argument that this isn?t a warrant. The documents are a series of internal emails from DOJ attorneys in the United States Attorney?s Office for the Northern District of California, the district where the order in Rigmaiden?s case was issued. The?emails make clear that U.S. Attorneys in the Northern California were using Stingrays but not informing magistrates of what exactly they were doing. And once the judges got wind of what was actually going on, they were none too pleased:
As some of you may be aware, our office has been working closely with the magistrate judges in an effort to address their collective concerns regarding whether a pen register is sufficient to authorize the use of law enforcement?s WIT technology (a box that simulates a cell tower and can be placed inside a van to help pinpoint an individual?s location with some specificity) to locate an individual. It has recently come to my attention that many agents are still using WIT technology in the field although the pen register application does not make that explicit.
While we continue work on a long term fix for this problem, it is important that we are consistent and forthright in our pen register requests to the magistrates?.
These emails, combined with the text of the disputed order itself, suggest agents obtained authorization to use a pen register without indicating they also planned to use a Stingray. Either at the time of the application or after the fact, the government attempted to transform that order into a warrant that authorized the use of a Stingray.
Judicial supervision of searches is most needed when the government uses new technologies to embark into new and unknown privacy intrusions. But when the government hides what it?s really doing, it removes this important check on government power. We hope the court sees its been duped, and makes clear to the government that honesty and a warrant are requirements to using a Stingray.
ORIGINAL LINK HERE
U.K. Home Office Draft Statutory Guidance on National Security Retention of Biometric Data
Public Intelligence
March 27, 2013 in Home Office
The following draft guidance was released by the U.K. Home Office on March 26, 2013 and concerns retention periods of biometric data in cases involving national security determinations.

Protection of Freedoms Act 2012: Draft statutory guidance on the making or renewing of national security determinations allowing the retention of biometric data
![]()
2. This guidance is to provide direction to any police force or other law enforcement authority regarding the retention and use of biometric material for national security purposes through the making or renewing of a national security determination (?a NSD?).
3. This guidance is issued pursuant to section 22 of the 2012 Act, which places the Secretary of State under a duty to give guidance about making or renewing of a NSD under the provisions set out in section 20(2)(a) of the 2012 Act.
4. This guidance is publicly available and, in particular, should be readily accessible by members of any police force or law enforcement authority seeking to extend the permissible period of retention, for national security purposes, of DNA profiles or fingerprints which they have hitherto retained.
Law enforcement authorities
5. Only a law enforcement authority listed under section 18E(1) of the Counter-Terrorism Act 2008 or specified in any order made by the Secretary of State under that section may make or renew a NSD.
Full Article
The Golden Gate Bridge is Watching You
Seth Schoen
EFF.org
March 29, 2013
Yesterday, the Golden Gate Bridge switched to all-electronic tolling. As of March 27, drivers entering San Francisco no longer have the option to pay the $6 cash toll to a human toll collector. Unfortunately, all of the bridge?s electronic payment options track the identities of those paying the toll, and all represent a loss of privacy for visitors or commuters entering San Francisco by car. The current implementation of electronic tolling here (and elsewhere) is unnecessarily privacy-invasive and represents a missed opportunity to collect tolls electronically in more privacy-friendly ways.
Since March 27, motorists entering San Francisco have three different payment options. One option involves recognizing an RFID token in the motorist?s vehicle, while the remaining two use a camera to photograph and recognize the license plate. (A cute new animation [YouTube link] from the bridge operator explains the options, though not their privacy consequences.)
Motorists can sign up for a FasTrak RFID token, placed on the dashboard or under the windshield of their cars. The FasTrak system has operated for bridge-toll collection in California since 1997 and been available as an option for paying tolls on the Golden Gate Bridge since 2000. FasTrak subscribers must register an account (giving their legal names and license plate numbers, among other information) and obtain a token; as a car passes through the toll gates, an RFID reader detects the token?s presence, reads its serial number, and debits the corresponding prepaid toll accounts. At the same time, a record is created in the FasTrak database.
They can also create a ?license plate account? tied to their license plate number, and pre-pay money into this account. When a motorist with no FasTrak token drives through the toll gates, a license-plate reading camera records an image of their license plate, recognizes the number, and causes the prepaid account to be debited.
Motorists who haven?t preregistered with either FasTrak or the license plate account system also have their license plates photographed as they pass through the toll gate. In this case, the Golden Gate Bridge toll operator will work with the Department of Motor Vehicles to send an invoice in the mail (akin to a parking or speeding ticket, but not including a fine or penalty). They must then pay the invoice by mail or online.
Yesterday?s change involved phasing out the traditional cash payment option, and expanding the use of existing license-plate recognition technology. As the Wall Street Journal explained last year in an in-depth report, this technology has become widely used by police and law enforcement, municipalities, and even private companies. (Just on the other side of the bridge, beautiful Tiburon, CA, already uses license plate readers to track every car entering or leaving via the few roads leading in and out of town.)
The Golden Gate Bridge already had license plate readers in place, but in the past they were used only to ticket motorists who tried to evade tolls; now, they?ve been made a routine part of the toll-collection infrastructure itself. Though the physical infrastructure hasn?t changed much, a significant shift has taken place in the purpose to which license plate recognition is being put?from a tool to catch a tiny minority of law-evaders to a routine, automatic part of the payment process. The privacy loss from creating a database of who crosses the bridge (and other toll roads and bridges across California) is considerable, though as the Journal noted, creating such records is only one example of ?how storing and studying people?s everyday activities,even the seemingly mundane, has become the default rather than the exception?. Subpoenas to access FasTrak data for purposes other than toll collection have become a trend?even in contested divorce cases.
The tragedy in all of this is that most of these privacy harms could have been (and could still be) avoided while still achieving the benefits of electronic tolling. Toll collectors just need to decide that not collecting the identities of those who?ve paid their tolls should be a priority. At the simplest level, FasTrak could easily allow people to purchase prepaid transponders for cash at a kiosk or grocery store, and use them without registering them to a particular vehicle or name?just as the Bay Area?s mass transit card, Clipper, does. (There are a number of other privacy and security concerns about FasTrak, which is using a pretty basic technology, perhaps since its design has changed so little over the fifteen years it?s been in use.)
There are also higher-tech privacy solutions available. David Chaum published a cryptographic technique thirty years ago that can be used for anonymous electronic payments with many of the properties of cash; dozens of refinements to Chaum?s methods have been discovered in the meantime, and there?s a thriving field of research on privacy-preserving electronic toll collection. Many modern designs allow much more complex forms of toll collection (like congestion and per-kilometer charges), yet without creating an extensive database of who went where when. Our 2009 white paper on locational privacy and transportation emphasizes some of the ways that technology can solve these problems without taking away the benefits of electronic payments?if transportation infrastructure providers and the public recognize that privacy needs to be protected.
UPDATE: An alert reader pointed out that FasTrak has a procedure for acquiring and activating a FasTrak token anonymously: it requires visiting the FasTrak Customer Service Center in downtown San Francisco in person (and periodically reloading cash value in person). FasTrak says
You can open your account with cash, money order, or cashier?s check. A Representative will be able to open your account without requiring customer name, address or vehicle information. (If you try to open an account online, your name, address and vehicle information will be required.)
This option could benefit from much more publicity (and convenience). But thanks are due to FasTrak for offering it.
texas chainsaw massacre nfl playoffs crystal harris Texas A Texas A&m cotton bowl Fiscal cliff deal
No comments:
Post a Comment